Security Analytics platforms
Updated: October 29, 2023
Security Analytics platforms are advanced solutions that leverage big data analytics and machine learning techniques to enhance cybersecurity operations. These platforms collect and analyze vast amounts of security-related data from various sources, including network logs, endpoint data, and threat intelligence feeds. By applying sophisticated algorithms, Security Analytics platforms can identify and prioritize potential threats, detect anomalous behavior, and provide real-time insights into security incidents. These analytics help security teams understand the scope and impact of potential breaches, enabling them to respond swiftly and effectively. Moreover, the platforms offer valuable threat hunting capabilities, allowing security professionals to proactively search for indicators of compromise and potential vulnerabilities. Security Analytics platforms play a pivotal role in bolstering an organization's cybersecurity posture, enabling proactive threat detection and response to combat the ever-evolving landscape of cyber threats.
See also: Top 10 Cloud Security Software
See also: Top 10 Cloud Security Software
2023. Gutsy launches with huge $51M seed to bring process mining to security
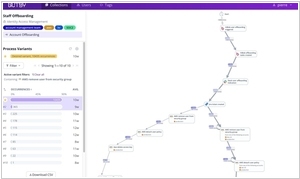
Gutsy, the startup that employs process mining techniques for security purposes, has successfully secured a seed funding round of $51 million. Traditionally, cybersecurity focused on detection and configurations, pinpointing misconfigurations or incident origins. However, Gutsy's unique approach is rooted in the concept that systems consist of interconnected processes. To truly comprehend any incident, understanding how these processes interlink is crucial. Similar to business process mining, which visualizes system connections, Gutsy allows you to identify breakdowns, such as in processes like staff offboarding. By grasping these interconnections, proactive measures can be taken to enhance the overall security of the company.
2020. Hunters raises $15M for its AI-based threat-hunting platform
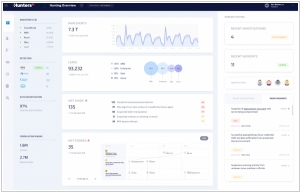
Hunters, a cybersecurity startup headquartered in Tel Aviv, specializes in assisting enterprises in defending against intrusions and analyzing cyber attacks. The company has recently secured a $15 million investment in a Series A funding round, with participation from Microsoft and other investors. By leveraging its SaaS platform, Hunters automates the traditionally manual process of threat hunting. The core concept revolves around leveraging data from an enterprise's diverse networking and security tools to identify stealth attacks.
2020. Uptycs lands $30M for its security analytics platform
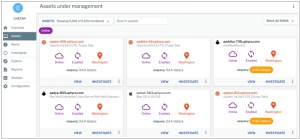
Uptycs, a startup specializing in security analytics, has recently secured $30 million in Series B funding. The investment aims to assist companies in effectively identifying and comprehending breaches as they occur. Uptycs focuses on resolving crucial security concerns including intrusion detection, compliance and audit, and incident investigation. These requirements are considered fundamental for security solutions within large-scale organizations, and the challenges they face vary accordingly. Uptycs adopts a flight recorder approach to security, providing security operations teams with the capability to analyze data and precisely understand the sequence of events leading to a detection and how intruders managed to bypass the company's defensive measures.
2020. Security decoy startup CounterCraft closes $5M Series A
CounterCraft, a company based in Spain specializing in developing B2B tools for gathering counterintelligence on evolving security threats, has successfully concluded a Series A funding round, raising $5 million. At the core of CounterCraft's product lineup is a "Threat Deception platform," which supports its customers' security operations by focusing on three key areas: threat detection, intelligence, and response. By utilizing deceptive techniques as a means of enticing attackers and gathering valuable intelligence, CounterCraft enables a more intelligent and effective response to threats. The platform provides a range of pre-configured use cases, including "Remote Worker Protection," "Pre-Breach Activity," "Sphere Phishing Response," and "Lateral Movement," covering all aspects of detection, intelligence, and response for each use case.